Malicious hackers are targeting people in the cryptocurrency space in attacks that start with a link added to the target’s calendar at Calendly, a popular application for scheduling appointments and meetings. The attackers impersonate established cryptocurrency investors and ask to schedule a video conference call. But clicking the meeting link provided by the scammers prompts the user to run a script that quietly installs malware on macOS systems.
KrebsOnSecurity recently heard from a reader who works at a startup that is seeking investment for building a new blockchain platform for the Web. The reader spoke on condition that their name not be used in this story, so for the sake of simplicity we’ll call him Doug.
Being in the cryptocurrency scene, Doug is also active on the instant messenger platform Telegram. Earlier this month, Doug was approached by someone on Telegram whose profile name, image and description said they were Ian Lee, from Signum Capital, a well-established investment firm based in Singapore. The profile also linked to Mr. Lee’s Twitter/X account, which features the same profile image.
The investor expressed interest in financially supporting Doug’s startup, and asked if Doug could find time for a video call to discuss investment prospects. Sure, Doug said, here’s my Calendly profile, book a time and we’ll do it then.
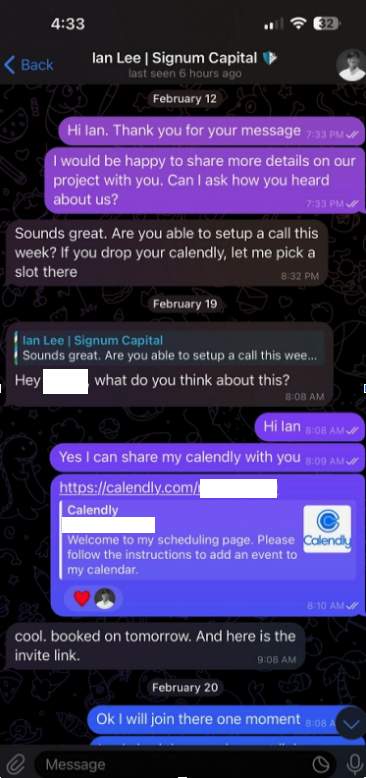
When the day and time of the scheduled meeting with Mr. Lee arrived, Doug clicked the meeting link in his calendar but nothing happened. Doug then messaged the Mr. Lee account on Telegram, who said there was some kind of technology issue with the video platform, and that their IT people suggested using a different meeting link.
Doug clicked the new link, but instead of opening up a videoconference app, a message appeared on his Mac saying the video service was experiencing technical difficulties.
“Some of our users are facing issues with our service,” the message read. “We are actively working on fixing these problems. Please refer to this script as a temporary solution.”
Doug said he ran the script, but nothing appeared to happen after that, and the videoconference application still wouldn’t start. Mr. Lee apologized for the inconvenience and said they would have to reschedule their meeting, but he never responded to any of Doug’s follow-up messages.
It didn’t dawn on Doug until days later that the missed meeting with Mr. Lee might have been a malware attack. Going back to his Telegram client to revisit the conversation, Doug discovered his potential investor had deleted the meeting link and other bits of conversation from their shared chat history.
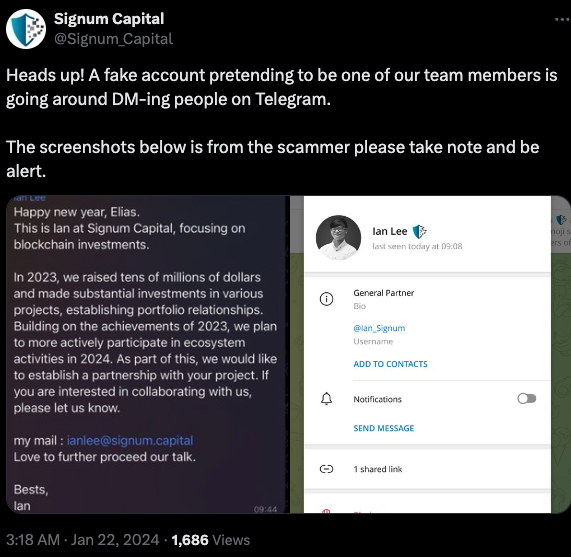
In a post to its Twitter/X account last month, Signum Capital warned that a fake profile pretending to be their employee Mr. Lee was trying to scam people on Telegram.
The file that Doug ran is a simple Apple Script (file extension “.scpt”) that downloads and executes a malicious trojan made to run on macOS systems. Unfortunately for us, Doug freaked out after deciding he’d been tricked — backing up his important documents, changing his passwords, and then reinstalling macOS on his computer. While this a perfectly sane response, it means we don’t have the actual malware that was pushed to his Mac by the script.
But Doug does still have a copy of the malicious script that was downloaded from clicking the meeting link (the online host serving that link is now offline). A search in Google for a string of text from that script turns up a December 2023 blog post from cryptocurrency security firm SlowMist about phishing attacks on Telegram from North Korean state-sponsored hackers.
“When the project team clicks the link, they encounter a region access restriction,” SlowMist wrote. “At this point, the North Korean hackers coax the team into downloading and running a ‘location-modifying’ malicious script. Once the project team complies, their computer comes under the control of the hackers, leading to the theft of funds.”
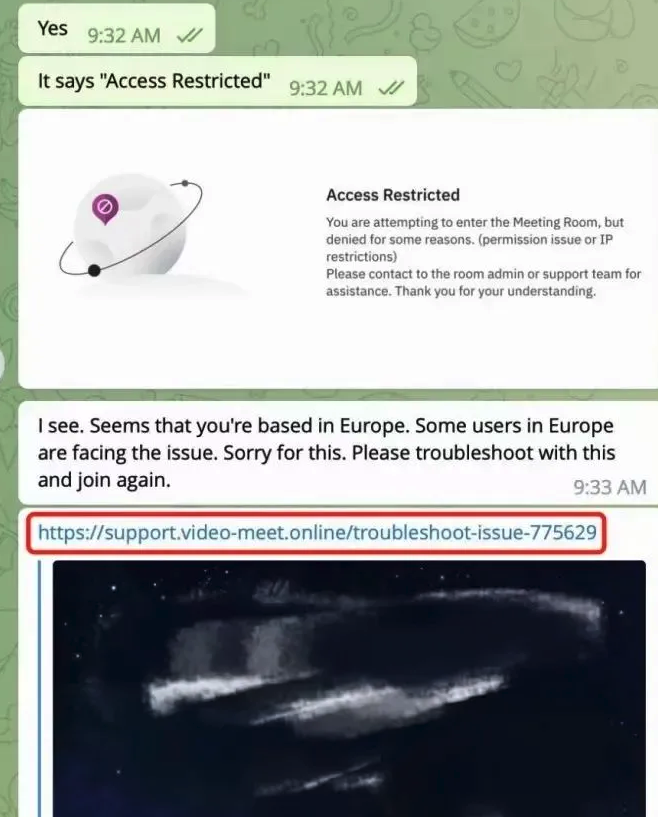
Image: SlowMist.
SlowMist says the North Korean phishing scams used the “Add Custom Link” feature of the Calendly meeting scheduling system on event pages to insert malicious links and initiate phishing attacks.
“Since Calendly integrates well with the daily work routines of most project teams, these malicious links do not easily raise suspicion,” the blog post explains. “Consequently, the project teams may inadvertently click on these malicious links, download, and execute malicious code.”
SlowMist said the malware downloaded by the malicious link in their case comes from a North Korean hacking group dubbed “BlueNoroff, which Kaspersky Labs says is a subgroup of the Lazarus hacking group.
“A financially motivated threat actor closely connected with Lazarus that targets banks, casinos, fin-tech companies, POST software and cryptocurrency businesses, and ATMs,” Kaspersky wrote of BlueNoroff in Dec. 2023.
The North Korean regime is known to use stolen cryptocurrencies to fund its military and other state projects. A recent report from Recorded Future finds the Lazarus Group has stolen approximately $3 billion in cryptocurrency over the past six years.
While there is still far more malware out there today targeting Microsoft Windows PCs, the prevalence of information-stealing trojans aimed at macOS users is growing at a steady clip. MacOS computers include X-Protect, Apple’s built-in antivirus technology. But experts say attackers are constantly changing the appearance and behavior of their malware to evade X-Protect.
“Recent updates to macOS’s XProtect signature database indicate that Apple are aware of the problem, but early 2024 has already seen a number of stealer families evade known signatures,” security firm SentinelOne wrote in January.
According to Chris Ueland from the threat hunting platform Hunt.io, the Internet address of the fake meeting website Doug was tricked into visiting (104.168.163,149) hosts or very recently hosted about 75 different domain names, many of which invoke words associated with videoconferencing or cryptocurrency. Those domains indicate this North Korean hacking group is hiding behind a number of phony crypto firms, like the six-month-old website for Cryptowave Capital (cryptowave[.]capital).
In a statement shared with KrebsOnSecurity, Calendly said it was aware of these types of social engineering attacks by cryptocurrency hackers.
“To help prevent these kinds of attacks, our security team and partners have implemented a service to automatically detect fraud and impersonations that could lead to social engineering,” the company said. “We are also actively scanning content for all our customers to catch these types of malicious links and to prevent hackers earlier on. Additionally, we intend to add an interstitial page warning users before they’re redirected away from Calendly to other websites. Along with the steps we’ve taken, we recommend users stay vigilant by keeping their software secure with running the latest updates and verifying suspicious links through tools like VirusTotal to alert them of possible malware. We are continuously strengthening the cybersecurity of our platform to protect our customers.”
The increasing frequency of new Mac malware is a good reminder that Mac users should not depend on security software and tools to flag malicious files, which are frequently bundled with or disguised as legitimate software.
As KrebsOnSecurity has advised Windows users for years, a good rule of safety to live by is this: If you didn’t go looking for it, don’t install it. Following this mantra heads off a great deal of malware attacks, regardless of the platform used. When you do decide to install a piece of software, make sure you are downloading it from the original source, and then keep it updated with any new security fixes.
On that last front, I’ve found it’s a good idea not to wait until the last minute to configure my system before joining a scheduled videoconference call. Even if the call uses software that is already on my computer, it is often the case that software updates are required before the program can be used, and I’m one of those weird people who likes to review any changes to the software maker’s privacy policies or user agreements before choosing to install updates.
Most of all, verify new contacts from strangers before accepting anything from them. In this case, had Doug simply messaged Mr. Lee’s real account on Twitter/X or contacted Signum Capital directly, he would discovered that the real Mr. Lee never asked for a meeting.
If you’re approached in a similar scheme, the response from the would-be victim documented in the SlowMist blog post is probably the best.
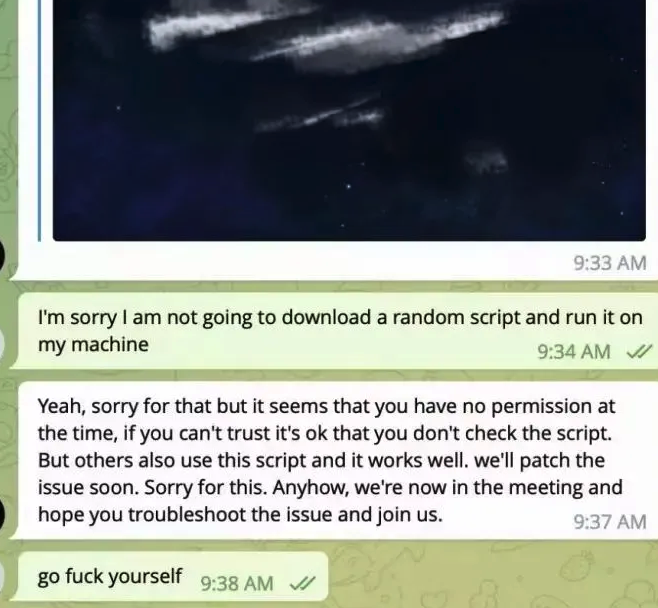
Image: SlowMist.
Update: Added comment from Calendly.




Do not have any Bitcoin but if I did I would probably be a nervous wreck.
Great reporting as usual.
It should be noted that folks need to be careful with reaching out via twitter to verify an individual. Lots of fake accounts on Twitter nowadays.
Also, kudos to not running some rando script and points added for the GFY sign off.
I’m probably not the only one who thought Mac’s were pretty much immune to attacks like this. I guess I’ll need to update my thinking. Are there reliable antivirus programs that will run on Macs that will block attacks like this? Or was it just too new?
Yes, there are commercial products that does this fairly well for the Mac, but I’m not going to flog them here. The one point I hoped to make with this post is that it doesn’t matter if you’re using Windows or a Mac — what matters is how careful you are about what you choose to install. In the end, no antivirus product is going to catch all attacks, and it is often the case that a certain number of their customers have to get owned by a new threat before it is flagged as bad. So there is generally a lag time for the AV vendors, and that lag time is usually not more than hours or days, but often that’s enough to infect a good number of victims before the attackers move on and switch things up again.
When there is money to be had in hacking a platform, I think you’re going to find NO platform is “immune”.
Mac’s are pretty immune to automated attack, but this is pure social engineering. create a phony meeting, create a phony problem, offer a phony solution that gets the user to do the work normally done by a trojan. Genius! As an IT professional the one thing we cannot fix is the space between the chair and keyboard.
“and I’m one of those weird people who likes to review any changes to the software maker’s privacy policies or user agreements before choosing to install updates.” Couldn’t agree more with this statement lol!
Would an app like sandboxie (for windows at least) provide a safe environment to run the Telegraph and/or virtual meeting software from?
Not installing random scripts from strangers is really the best method to avoid this particular issue.
BK,
RE: “I’m one of those weird people who likes to review any changes to the software maker’s privacy policies or user agreements before choosing to install updates.”
Perhaps you can give us a heads up in future articles when/if you find EULAs that are particularly egregious.
Excellent report !
mashable dot com/article/x-twitter-elon-musk-bots-fake-traffic
“According to CHEQ, a whopping 75.85 percent of traffic from X to its advertising clients’ websites during the weekend of the Super Bowl was fake.”
= Twitterx can die now, it’s ok. We have alternatives.
Sounds like it’s malware that’s operating on the honor system – they send you the script and ask you to run it.
If someone wants to use some video meeting software that doesn’t work, I’ll send them a Google Meet link. It always works, with no setup required. If they don’t want to use Google Meet, they can get lost.
The other comment that assumes that “Macs are immune to attacks” is ludicrous. Every system can be attacked if you have enough resources to find or buy zero-days. iPhones have hundreds of them – how do you think Pegasus continues to operate year after year?
The real question is: Why is he accepting and doing business stuff on Telegram? Would you take someone seriously if they email you as an investor from a Gmail account? Of course not. Faking a corporate email account and website is way harder to pull off because those are paid services, and they need to pass all sorts of payment verification, and even if they do to manage to fake a complete website every few days (because providers take them down quickly when reported), which is cost expensive, you can verify the domain to their linked Twitter or LinkedIn account and see how it does not match the real company domain.
I get it, it’s a startup, but there is a reason why more established companies do not use instant messaging systems for customer communications in the first place. They use them for internal use or for less critical things or that don’t require any sort of verification.
They use email for everything else because email at least is harder to fake. Even phone numbers and voice can be faked, which makes email the securest way to deal today online.
Faking an email account from something at something@microsoft.com is next to impossible for a scammer. You can fake the headers, but not the real sender.
So if someone says they work for Microsoft, great, please invite me to the meeting by email. It’s standard procedure to accept invites only by email. There is a reason the corporate world still uses Outlook. If the email invite comes then from Gmail with some excuse they are travelling and can’t access their regular email account…you can already smell something is off. Any supposed tech or investor company will at least have a website and some social profiles with followers (which is also harder to fake, so they just link to real social profiles assuming you will not contact them) that you can match the domain as well.
This leads to another part. If you have social media accounts for a company, you should put your domain on it, always. That way, other people can verify impersonators and people using ID theft to scam others. No need to put your email account but do link to your official startup or company website.
Side point, Twitter and LinkedIn are somehow more professional than Telegram?
I’d call that an opinion based on a previous marketing point from each…
Signal, Telegram, Whatsapp, Discord, Mastodon, these are all as valid as the other
AFAIK in terms of the company actually doing backside work to verify each user,
no doubt with exceptions and unknowns in terms of internal processes…
but the point being you couldn’t “really trust” any of them or even 2-3 combined.
Whether an offline investor type reaching out below the official radar would
choose one to the next shouldn’t itself really be the red flag. If someone DM’ed
on Twitter or LinkedIn I’d personally be just as suspect of that provenance as email.
“Would you take someone seriously if they email you as an investor from a Gmail account?”
Compared to Twitter / LinkedIn?! (I know old Angel investors with OG AOL/Yahoo accounts…)
Tens/hundreds of MILLIONS use Gmail for business as legit as any. Vetting isn’t simple.
The fail is to accept any single authentication yet be comfortable moving to the next step.
Gmail is hardly below Twitter/LinkedIn standards… verification can’t stop there either way.
It’s a shame “Doug” wasn’t conversant with witchcraft and demonology. One of the main tenants of the art was that the evil spirits couldn’t come in unless you INVITED them in. Practitioners know that running a script is akin to casting a spell saying “Come in!” and the evil spirits will entice you with convincing jabberwocky like “Please refer to this script as a temporary solution.”
We see this again and again biting us. There is no commercial product that can protect against this kind of security weakness, IMHO. The most secure air-gapped system or network is subject to compromise by the wetware, and any who don’t believe that, meditate on Stuxnet…
Excerpted from the scammer screenshot in Signum Capital’s warning,
“Love to further proceed our talk.
Bests,
Ian”
Non-standard English. Shields up right there.
Pls I want no how to make money